SEC Cybersecurity Rules: What CISOs Need To Know
SEC has adopted rules on cybersecurity for disclosures about incidents, risk management and governance.
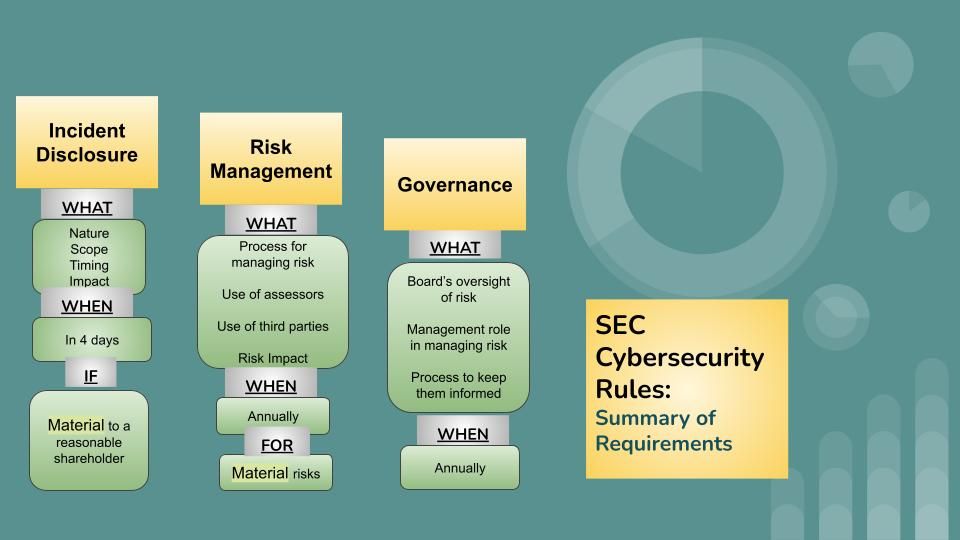
In one of the most notable exercises of legal authority in the domain of cybersecurity, the Securities and Exchange Commission (SEC) this week adopted rules requiring public companies to disclose cybersecurity incidents as well as provide annual disclosures on their risk management and governance.
What do the rules require?
The rules can be broken down into three key requirements:
- Incident Disclosures: Companies must disclose when they experience a material cybersecurity incident, and must do so within four business days of determining the materiality. The disclosure should describe the material aspects of the nature, scope, timing, and the material impact of the incident.
- Risk Management: Companies must also annually disclose their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats in sufficient detail for a reasonable investor to understand those processes.
- Governance: Companies must also annually disclose the board’s oversight and management’s role in assessing and managing material risks from cybersecurity threats, and the process of how they are kept informed.
What is SEC's intent?
The intent of the rules is to better balance investors’ needs and company's cybersecurity posture. The SEC wants to avoid delayed reporting of cybersecurity incidents that can result in mis-pricing of securities, which in turn can be exploited by threat actors, employees, related third parties, and others through trades made before an incident becomes public.
Central to these requirements is the concept of materiality. The SEC requires that the company shall make a materiality determination regarding a cybersecurity incident without unreasonable delay after discovery of the incident.
According to the standard used by the SEC, information is material if “there is a substantial likelihood that a reasonable shareholder would consider it important” in making an investment decision, or if it would have “significantly altered the ‘total mix’ of information made available.”
What constitutes material impact?
The SEC recognizes that a company may not have complete information about the incident but may know enough about the incident to determine whether the incident was material. The focus of the disclosure is primarily on the impacts of a material cybersecurity incident, rather than on requiring details regarding the incident itself.
Among the examples of material impact are harm to a company’s reputation, customer or vendor relationships, or competitiveness. Similarly, the possibility of litigation or regulatory investigations or actions may constitute a reasonably likely material impact to the company. The SEC expects that most organizations’ materiality analyses will include consideration of the financial impact of a cybersecurity incident, so information regarding the incident’s impact on the registrant’s financial condition and results of operations will likely have already been developed.
What about risks of over-disclosure?
It is important to note that the incident disclosure requirement would not extend to specific, technical information about the incident’s remediation status, whether it is ongoing, and whether data were compromised, or the company’s planned response to the incident or its cybersecurity systems, related networks and devices, or potential system vulnerabilities in such detail as would impede its response or remediation of the incident.
As a specific example, the proposed rules included whether the company undertakes activities to prevent, detect, and minimize effects of cybersecurity incidents, whether it has a business continuity, contingency, and recovery plans in the event of a cybersecurity incident, and whether previous cybersecurity incidents have informed changes in the registrant’s governance, policies and procedures, or technologies. However, these requirements were removed from the final rule.
How does it apply to 3rd party systems?
Depending on the circumstances of an incident that occurs on a third-party system, disclosure may be required by both the service provider and the customer, or by one but not the other, or by neither.
The rules do not require that companies conduct additional inquiries outside of their regular channels of communication with third-party service providers pursuant to those contracts. In other words, the information available via the disclosure controls and procedures already in place would be used as the basis to determine the materiality of the incident.
What detail is sufficient for risk management disclosures?
When describing their risk management processes, companies should address:
(i) Whether and how any such processes have been integrated into the registrant’s overall risk management system or processes;
(ii) Whether the registrant engages assessors, consultants, auditors, or other third parties in connection with any such processes; and
(iii) Whether the registrant has processes to oversee and identify such risks from cybersecurity threats associated with its use of any third-party service provider.
Companies should also describe whether any risks from cybersecurity threats, including as a result of any previous cybersecurity incidents, have materially affected or are reasonably likely to materially affect them, including their business strategy, results of operations, or financial condition and if so, how.
Is SEC mandating a risk management strategy?
The SEC clarifies that the purpose of the rules is to inform investors, not to influence whether and how companies manage their cybersecurity risk. The SEC further clarified that risk quantification or other quantifiable metrics are not considered a mandatory element of the cybersecurity disclosure framework.
Similarly, the rules don't expect you to disclose what you don't know about. The focus remains on avoiding delayed disclosure of known material cybersecurity risks which results in mis-priced securities that can be exploited through trades made before an incident becomes public.
What steps are required for compliance?
An organization that is already subject to and meets compliance requirements under other laws like HIPAA or GDPR should have the necessary processes and systems in place to meet with the bulk of the requirements under these rules. The major additional undertaking would be the determination of materiality under the SEC standard.
For e.g., requiring that a material incident be disclosed under SEC rules in 4 days is no more onerous than requiring a breach disclosure in 72 hours under the GDPR. However, the SEC requirements are distinguished from similar requirements found in HIPAA or GDPR because of their focus on the consequences for the company that are material to investors, and whose timing is tied not to discovery but to a materiality determination. In contrast, a breach notification under HIPAA or GDPR focuses on the consequences for the affected individuals.
Similarly, requiring that companies provide disclosures about risk management and governance annually is not an additional burden for most public companies with mature cybersecurity programs that already undergo a SOC-2 or ISO-27001 audit annually. Those audits require companies to maintain documentation about their risk management and governance processes. However, that documentation may need to be tailored to focus on material risks in sufficient detail for a reasonable investor to understand those processes to meet SEC requirements.
In conclusion, the SEC rules would help improve the timely reporting of cybersecurity risks material to investors, while at the same time strengthen the risk management and governance practices of organizations. For those who already have a mature cybersecurity program, only minor changes may be required to comply. For others, it presents an opportunity to improve their maturity by putting in place processes that can help meet the requirements.
Connect with us
If you would like to reach out for guidance or provide other input, please do not hesitate to contact us.
